Raising awareness of the value of corporate data and its protection is increasingly important. In today's business landscape, there are some best practices that your company should follow to make IT security as robust as possible.
1) Use security frameworks
Information security frameworks, such as ISO 27001, are procedures that can help you in the proper management of your company to prevent and deal with cyber attacks.
Even if you cannot perform all the procedures indicated by these certifications, you can adopt some of the practices indicated to strengthen your computer security.
2) Establish a risk assessment checklist
It implements a regular risk assessment process through a checklist.
The checklist must contain:
- The objective of the evaluation (e.g. whether certain safety procedures are being followed correctly by your employees);
- The evaluator;
- The degree of risk associated with not following that procedure;
The checklist helps you to monitor all aspects of security, without the risk of forgetting any (with unpleasant consequences).
3) Use the information obtained to prevent attacks
Risk assessment through checklists provides useful information on the most likely threats and areas for improvement.
Remind your team to correct malpractices and maintain good security habits, so as to prevent the occurrence of cyber attacks using familiar methods.
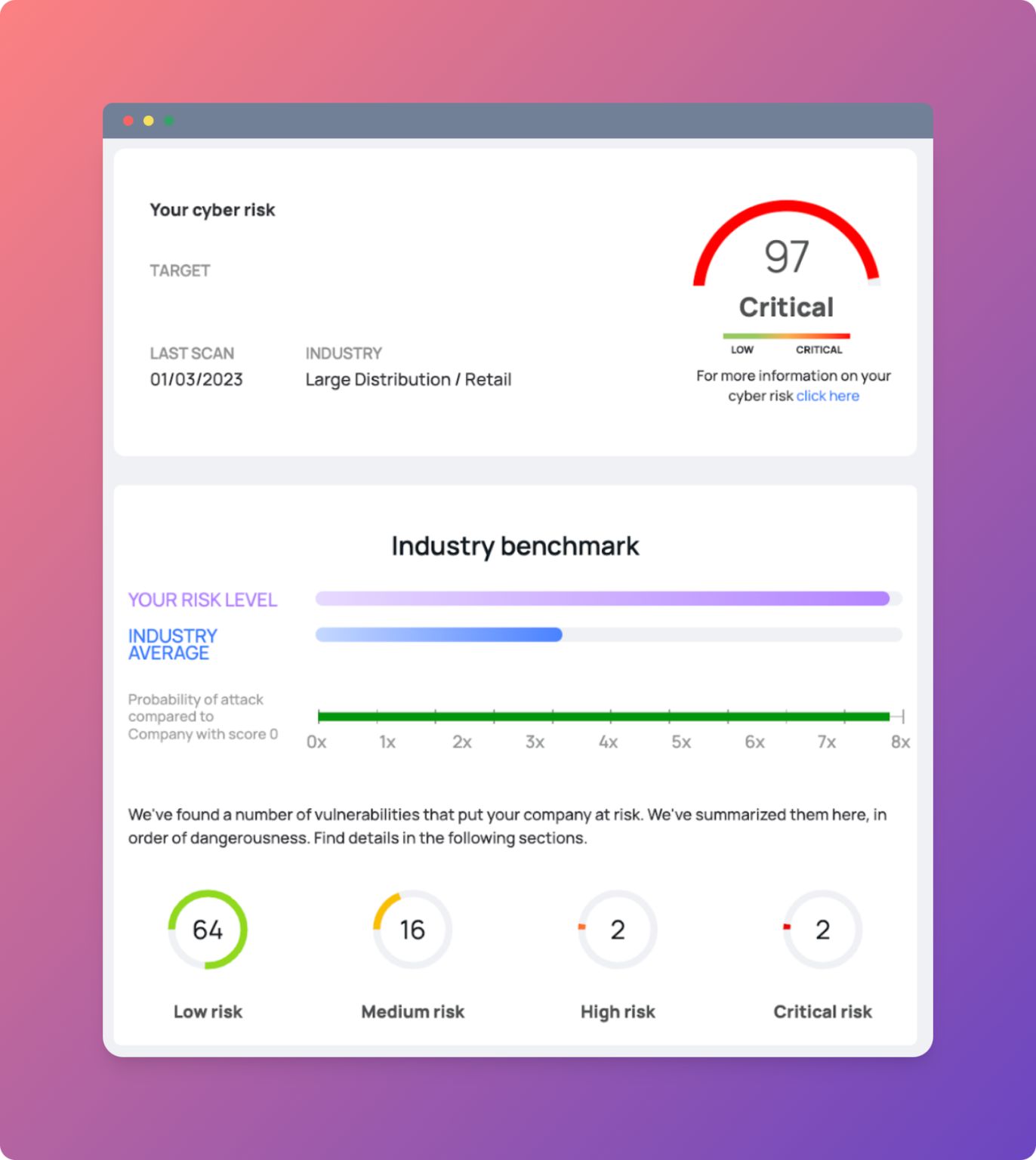
4) Penetration testing for vulnerability insights
Also periodically carry out in-depth analyses of your company's vulnerabilities and be protected against new threats (and you can do so for free on our platform).
It can help you to think as if you were a hacker and think carefully about how you would attack the company.
This practice can help you understand whether your business is well defended against external attacks.