The types of cyber attacks against companies are evolving almost daily and hackers are becoming increasingly unpredictable.
This is why ongoing cyber security is so important. A cyber attack against your company can lead to:
- Loss of sensitive data
- Data theft and blackmail
- Huge costs of recovering stolen data
- Damage to reputation
- legislator's fines for adequate cyber defences
- Closure of the activity (in serious cases)
In order to avoid such damage, we need to dispel three myths about computer security:
- Antivirus software is enough... FALSE.
The truth: Traditional IT security solutions, such as antivirus and firewalls, are not sufficient.
First of all, you need to make sure that they are always updated by your IT security manager, otherwise they will not be able to stop the new viruses that come out almost every day.
Moreover, antivirus does not guarantee you any security in the event of a cyber attack. What do you do if your company is attacked and your computers are rendered unusable? How do you restore the smooth running of your company?
For this reason, having real cyber security is a job that has to consider many more aspects.
- Computer security is only a technical issue.... FALSE
The truth: The most widespread and most effective computer attacks are actually directed at people. Viruses that are technically easy to block can still be very harmful if they are installed by the carelessness of an employee, who clicks on a dangerous and misleading link and authorises the installation.
Therefore, CEOs should ensure that they also have cyber security procedures for employees and their online behaviour.
- Just monitor once in a while... FALSE
The truth: New viruses are created almost every day, along with new methods of installing them on company computers.
Monitoring one's own IT security once in a while is not enough.
The entrepreneur or the security manager must have a constant and always up-to-date procedure for checking IT systems.
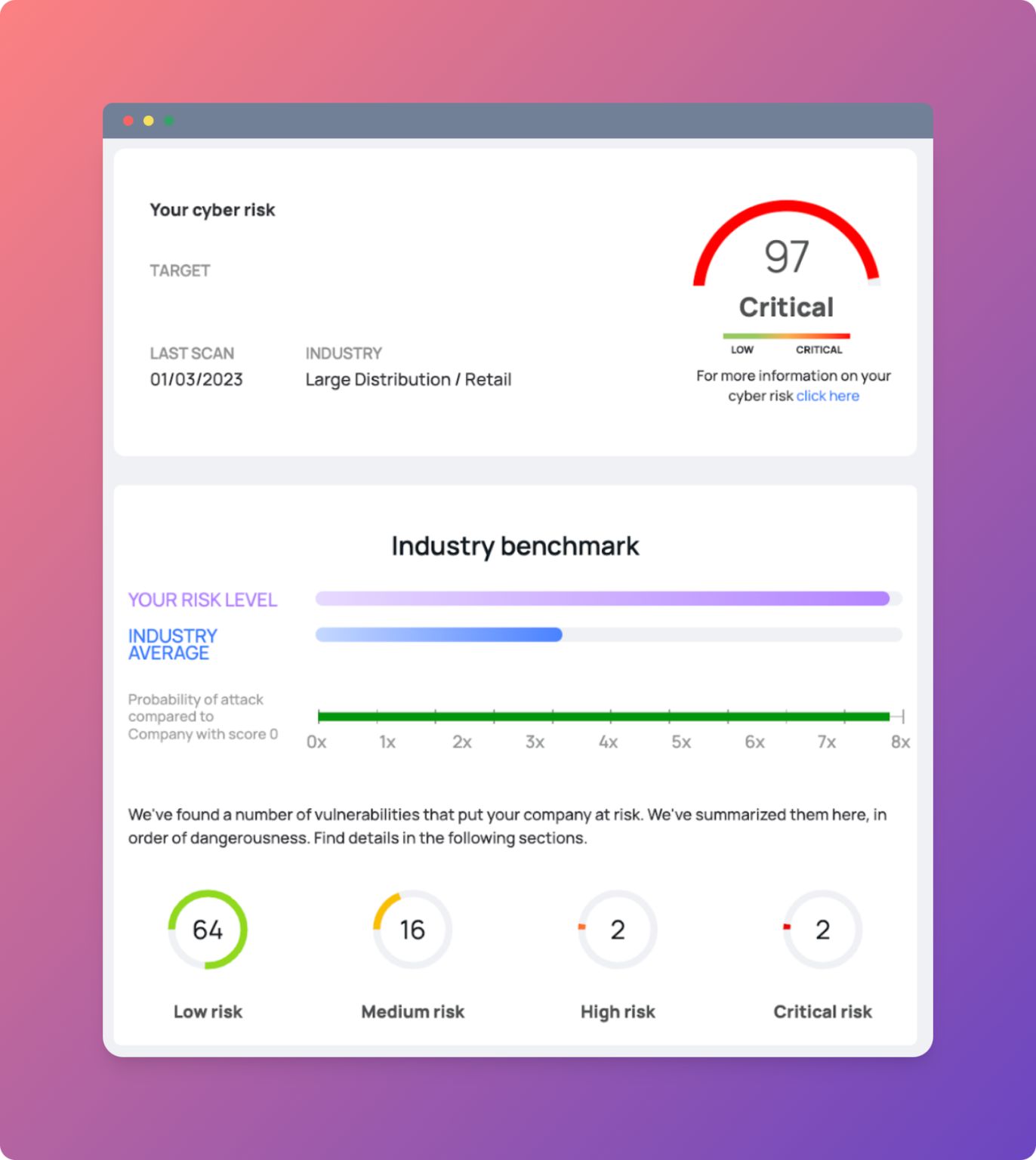
It should also generate analysis reports at least every month, to highlight:
- Number of incidents solved;
- Speed in resolving incidents;
- The potential business impact of these incidents;
- current threat data
- any required external consultancy work
And everything you need to constantly monitor the health of your cyber defences.
Considering all these factors, it is important to protect one's business in the best possible way.
To protect your company and insure yourself against the damage of cyber attacks, sign up for free to our Cyberangels platform: