If you are a manufacturer, distributor or supplier in today's global economy, protecting yourself from cyber risks is more important than ever.
In this blog, we have written several articles that can help you address the issue, if you have not already done so.
Many companies have begun to adopt internal cybersecurity best practices throughout the organisation, including implementing an enterprise risk management (ERM) programme and conducting regular cyber risk assessments.
But it is important to remember that suppliers are also at risk.
The cyber risk associated with the supply chain is one of the Main emerging risks facing organisations today.
For every company today, it is crucial to recognise the relationship with its suppliers as potentially risky. It is no exaggeration to say that supplier risk can have a significant impact on a company's success or failure.
But how can you evaluate the risk of your suppliers? And what to do if I am not up to it?
With the advent of globalisation, it is becoming increasingly difficult for companies to manage supplier risk. The number of suppliers has increased, as has their geographical distance from headquarters. Companies have also found themselves dealing with multiple suppliers in different countries and regions, which adds another layer of complexity to the process.
In this article, we will examine some of the main types of risk that suppliers may present and how to mitigate them.
Supplier-related risks: where to start
It is important to note that a company's risk analysis must be conducted on an ongoing basis. The process of identifying, assessing and mitigating potential risks should not be seen as a one-off activity.
Rather, it should be seen as a continuous process that begins with the identification of potential risks and evolves as the company grows.
The first thing to do is survey the various professionals and companies from which your departments now buy products and services and create a list of all suppliers used by the company, both direct and indirect. Make sure you don't leave any out.
Once the suppliers have been identified, it is necessary to understand what they do in your business process and how they do it, including their capabilities, business diversification, geographical location and more.
It is appropriate to proceed with a shared assessment within the company on the 'strategic' nature of the supplier. How much does this impact on my business and especially what kind of problems could affect their ability to deliver the expected performance?
The next step is to perform a supplier's cyber risk assessment. You can use tools or hire experts to conduct classical evaluations such as vulnerability scans or penetration test.
If you want to make a simple risk assessment, you can use the following checklist:
- Check their website for open ports and other vulnerabilities.
- Check that there is a security certificate on their website and, if not, ask them to install one.
- Check their website for a privacy policy on how they handle your data.
- Ask what protocols are used for communication between their servers and yours (e.g. HTTPS or SSH).
Where possible (depending on how deep your practice is on the subject or the stage of the supplier's own view cycle), you can also conduct an assessment - shared with the supplier - of its security positionincluding its adherence to security standards (e.g. ISO 27001) and best practices (e.g, NIST).
To this end, you can conduct interviews with suppliers or check publicly available resources, such as their website or LinkedIn profile
There are automated solutions on the market for these aspects as well: most of the time, questionnaires are sufficient to delve into topics that are difficult to detect by automated analyses such as those in the previous points.
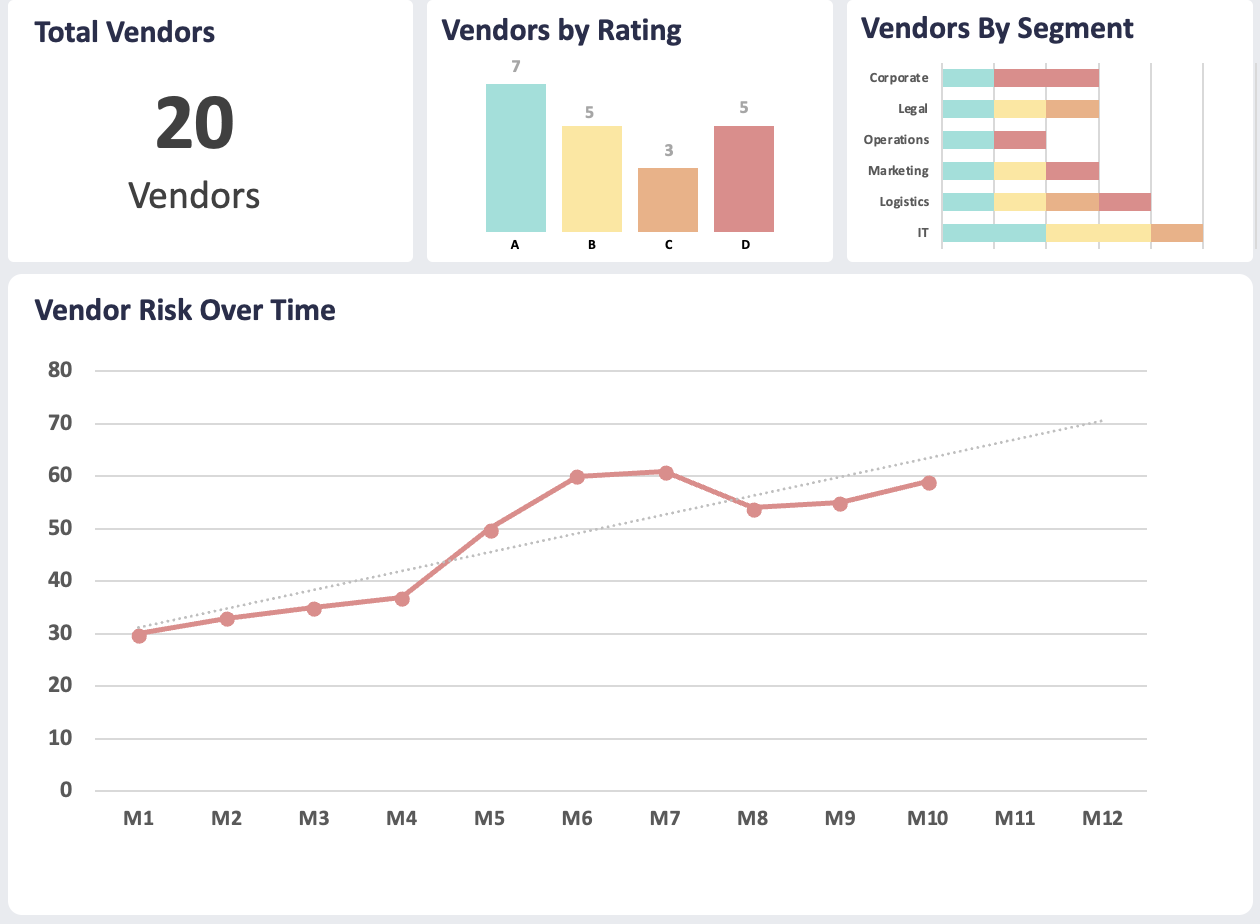
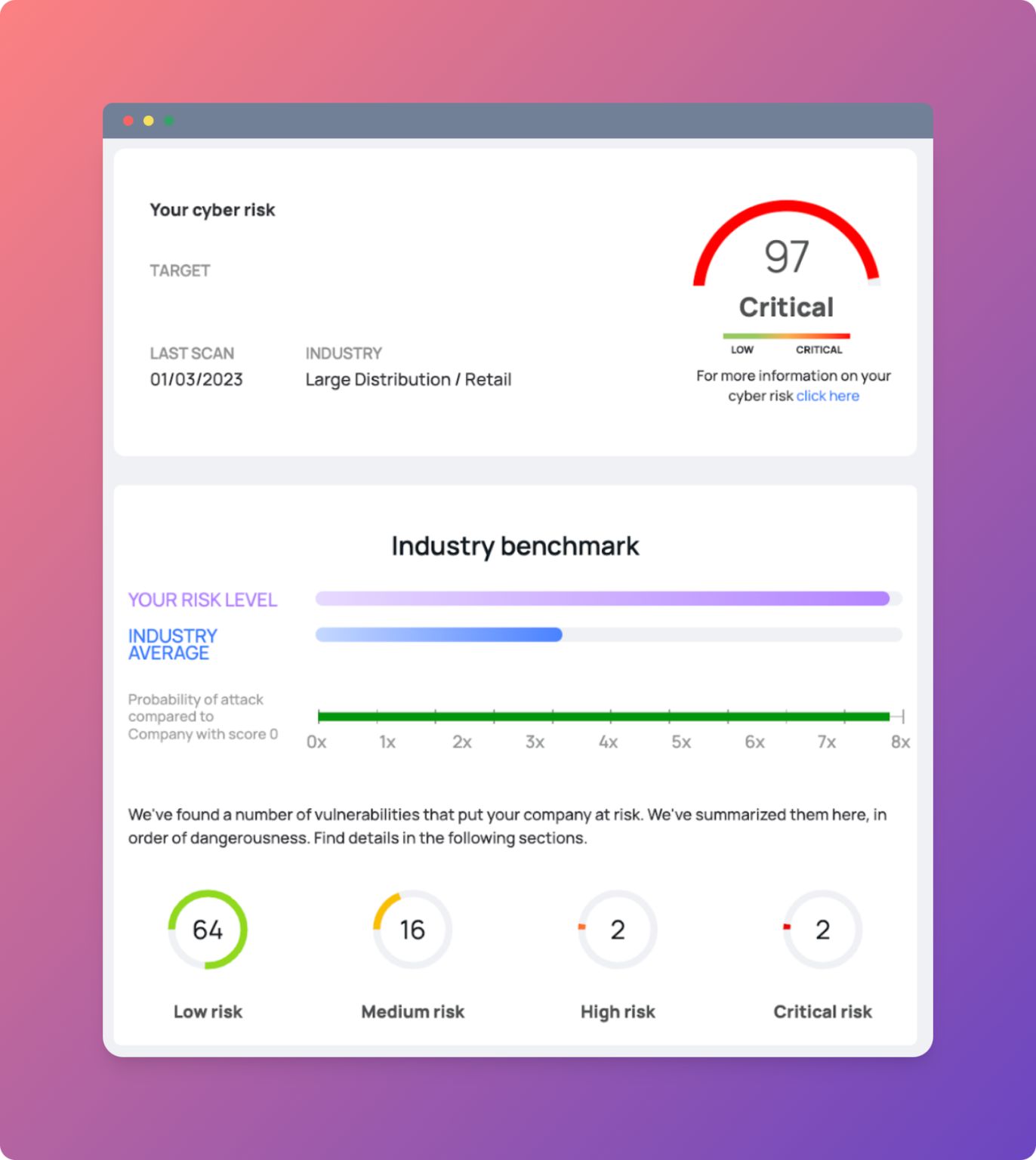
Once aware of supplier-related cyber risks, the last step is to build your Vendor Cyber Rating. It is a summary parameter on supplier reliability constructed through the analysis of the main factors concerning the health of a company, the level of risk management and the level of dependence on the customer.
Developing an action plan
At this point it would be ineffective to stop there! It cannot be enough to have performed an initial analysis: cyber risk is constantly evolving, hand in hand with the evolution of technologies.
It is therefore important develop an action plan based on the results obtained.
The action plan must include a list of actions to be taken in a shared manner with your supplierfrom the most urgent to those that can wait. You must also specify when and how each task will be completed and who is responsible for its implementation. This plan should give you a clear idea of what to do next and when.
For example, if your supplier is not compliant with data protection regulations, what measures will you take to solve the problem? You may want to re-evaluate the contract with the supplier or implement new processes to ensure compliance.
Once the plan is in place, it is necessary to update it regularly. If a task is completed early or late, add or remove it from the schedule if necessary. It may also be necessary to change the order of actions, as some tasks may be easier or more urgent than others.
Conclusions
By following these suggestions, it will then be possible for the customer to know which suppliers are best suited to its needs and requirements, in order to keep a portfolio that is as accurate as possible so as to limit the company's operational risk resulting from the cyber inadequacy of its suppliers.
How Cyberangels helps you
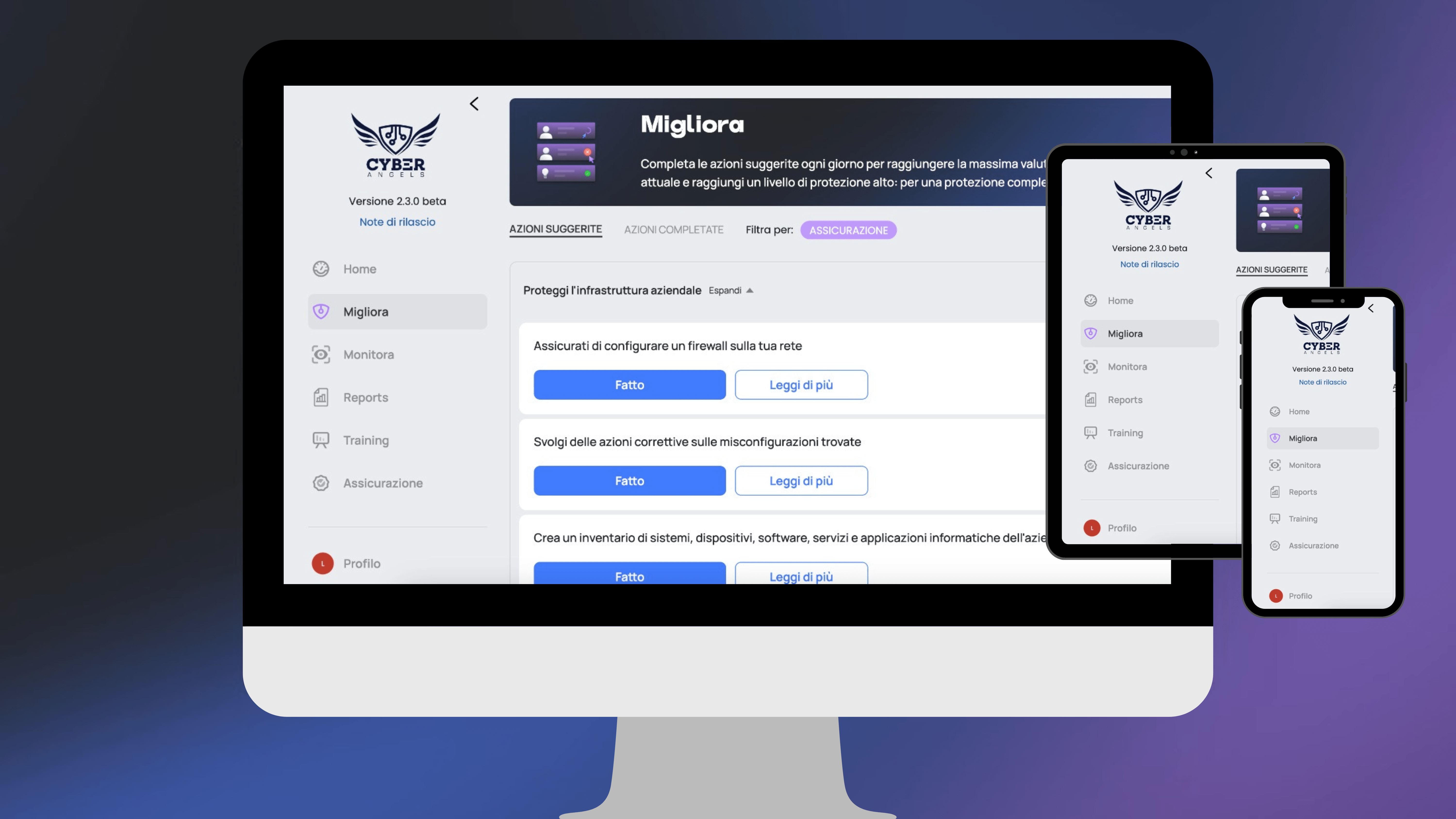
The new solution Cyberangels - Third Party Risk Management (CBR - TPRM) can help you manage and automate the steps described in this article.
CBR - TPRM was born from the experience gained over the years, from having helped thousands of professionals, micro and small to medium-sized enterprises to become more resilient to cyber risk, without spending a fortune. The solution features:
- A web platform, accessible from any device and without installation.
- One automated tool for performing due diligence on suppliers, with the possibility of integrating it into their own systems.
- A integrated dashboard which allows you to monitor all relevant data relating to each supplier.
- A proprietary engine for calculating Vendor Cyber Rating which analyses the main factors affecting the health of a supplier, the level of cyber risk management and the level of dependence on the customer, calculated on the basis of automatic assessment and sector trends, i.e. information concerning the company's position in relation to the relevant sector.
If you still have any doubts about how to undertake a proper risk audit of your suppliers, we hope this article has provided you with enough information to understand why it is important and how to get started.
For any additional information, contact our team. Let Cyberangels you differentiate yourself from the competition: keep focusing on your business challenges, we'll take care of your security!