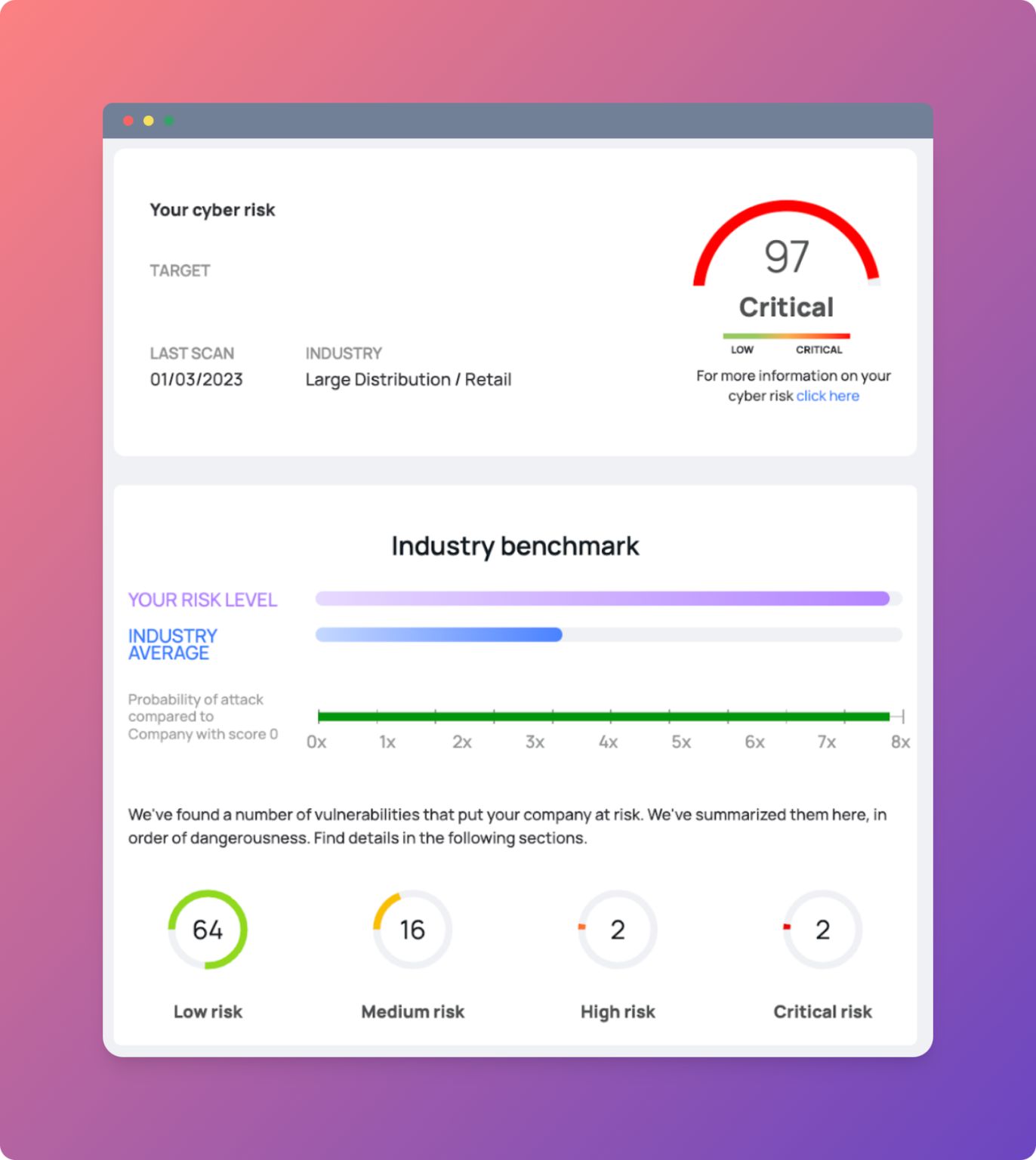
They want to convince us that IT security is a top priority for companies.
According to recent research, the growth trend in the annual expenditure that companies will devote to cybersecurity is set to increase by 15% per year, to reach USD 10 trillion in 2025.
Women entrepreneurs, managers, board members and M&A practitioners agree that they are "very concerned“: The frequency of cyber attacks has increased in recent years and the security measures put in place by companies are often not sufficient to protect them from threats.
In addition, most companies suffer at least one cyber attack per year and the figure becomes dramatic if the focus is on SMEs: in 2021, according to a report by ENISA (European Cyber Security Agency), the 46% of European companies was hacked.
For these reasons, cybersecurity would seem to have become an investment priority.
But are we really convinced?
In our opinion not true!
This is the feeling one gets when confronted with the endless stream of news stories about cyber attacks and data breaches at all levels of role and company size.
SMEs only become interested in cybersecurity when they suffer an attack.
What to do before considering an investment in cybersecurity
How can one blame the decision-makers, who in the face of the continuous news feed, then find themselves in difficulty in juggling among the endless supply of products and services on the market?
The topic of cybersecurity is becoming increasingly complex and requires careful planning and execution before it can be addressed.
When deciding to invest in cybersecurity, several questions must be answered: What is the company's risk profile? What vulnerabilities need to be addressed and how can they be tackled? And again, what types of attacks could occur in the future?
The team Cyberangelshas prepared this vademecum to help SMEs make a coherent preliminary assessment of how much they should invest in cybersecurity, according to their budget constraints.
In summary, by following our guide, you can create a solid plan that will help you protect your company from future attacks, while saving on unnecessary expenses such as hiring external consultants or purchasing expensive software solutions.
Let us begin.
Step 1 - Understand the risks to your company
First, it is crucial to understand what risks your company faces and what you can do to reduce them.
Risks are potential dangers or threats that could harm the company. In the context of cybersecurity, risks generally fall into two categories: interiors and exteriors.
Examples of internal risks are employees accidentally downloading malware onto their work computers or being careless with sensitive data stored on their laptops when they leave work for the day, or inadvertently transferring a supplier to a scam IBAN.
External threats, on the other hand, include all instances where malicious attackers exploit vulnerabilities in website applications or software running on networked systems; viruses that infect desktop computers through e-mail attachments; ransomware that locks critical data until payment is made in bitcoin; and malware that steals user credentials after clicking on a malicious link sent from an e-mail address apparently belonging to a known person (but which is not).
The list goes on...
Here are some questions you should ask yourself:
- What are the threats we face?
- How can we measure our exposure to these threats?
- What is the likelihood of a particular threat materialising into an actual attack?
- How quickly could we recover from an accident?
A key element in risk assessment is the extent of one's attack surface. We talked about it hereI suggest you give it a quick read.
Step 2 - Choose effective cybersecurity measures to reduce potential damage
Having understood what risks the company is subject to, it is now easier to prioritise the solutions most in line with one's profile and invest in this direction.
The time has come, therefore, to select and adopt cybersecurity measures sufficient to ensure that an accident does not cause serious damage.
You will need to consider how much it will cost to implement them and how much value they will add to your company in terms of protecting against threats and preventing damage from attacks.
It must be ensured that these measures are proportionate to the risk and implemented in a timely manner, without neglecting a critical factor: it is essential to test and update them regularly.
It is precisely for this reason that the evaluation of cost-effectiveness must be weighed not only in the light of the initial cost.
The main cost factor is the effort required to implement and maintain the solutions used by the company.
Companies often find it difficult to prioritise spending on different types of cyber protection initiatives due to the limited resources available in their budgets, which may lead them to invest heavily in one area but neglect others that could potentially prove just as valuable when the time comes for an attack against their systems.
For example, it is well known how 90% of cyber attacks are successful due to carelessness or superficially done activity: you quickly responded to a request from a well-known supplier to send a transfer to a new IBAN and found your company bank account relieved of a few tens of thousands of euros!
Therefore, investing in measures that can help prevent attacks such as phishing attempts and develop the necessary sensitivity in employees not to fall victim to scam sites or emails that lead to the spread of ransomware or malware with often notorious consequences in terms of lost money.
Step 3 - Activate vulnerability and threat monitoring.
Once the priorities of the measures have been identified, the next step is to activate the selected measures and practices.
At this stage, it will be important to document the established work plan so that the same strategy and objectives can be shared with possible suppliers.
In addition, a clear presentation of the security plan will allow you to keep costs under control: you decide whether and how much to spend on your security and not your suppliers!
Step 4 - Repeat everything
Creating a solid cybersecurity strategy is not a one-time thing, but an ongoing process.
At the end of the day, one must always remember that cybersecurity is a never-ending process.
Your cybersecurity strategy must be updated regularly and in response to changing circumstances, evolving threats and new technologies.
A good way to keep track of all these aspects is to have an internal team capable of analysing threats and vulnerabilities on an ongoing basis, so that you do not have to wait for the next important meeting or quarterly report to identify potential problems.
How does Cyberangels help you?
All our subscriptions include the route we have described in this article.
For all premium users of the platform, Cyberangels creates a customised cybersecurity strategy based on the company's characteristics: risk level, awareness, sector and organisational complexity.
Designed in Italy, it relies on international frameworks and standards (such as the Nist Cybersecurity Framework) to develop a cyber protection model for SMEs:
- From the identification of your company's risks,
- To customised action plans of reactive and proactive actions
- To the prioritisation of suggested interventions to optimise your budget constraints
- With the support of security experts at your disposal to implement the measures you have identified
- And finally, cyber risk insurance of absolute value.
Conclusion
We hope this article has provided enough information to understand why it is important to start thinking seriously about a small investment in cybersecurity and what the first steps should be.
For any additional information, contact our team and find out with us how to become as safe and secure as a large company, without having to spend capital or hire specialists.
Let Cyberangels you differentiate yourself from the competition: keep focusing on your business challenges, we'll take care of your security!