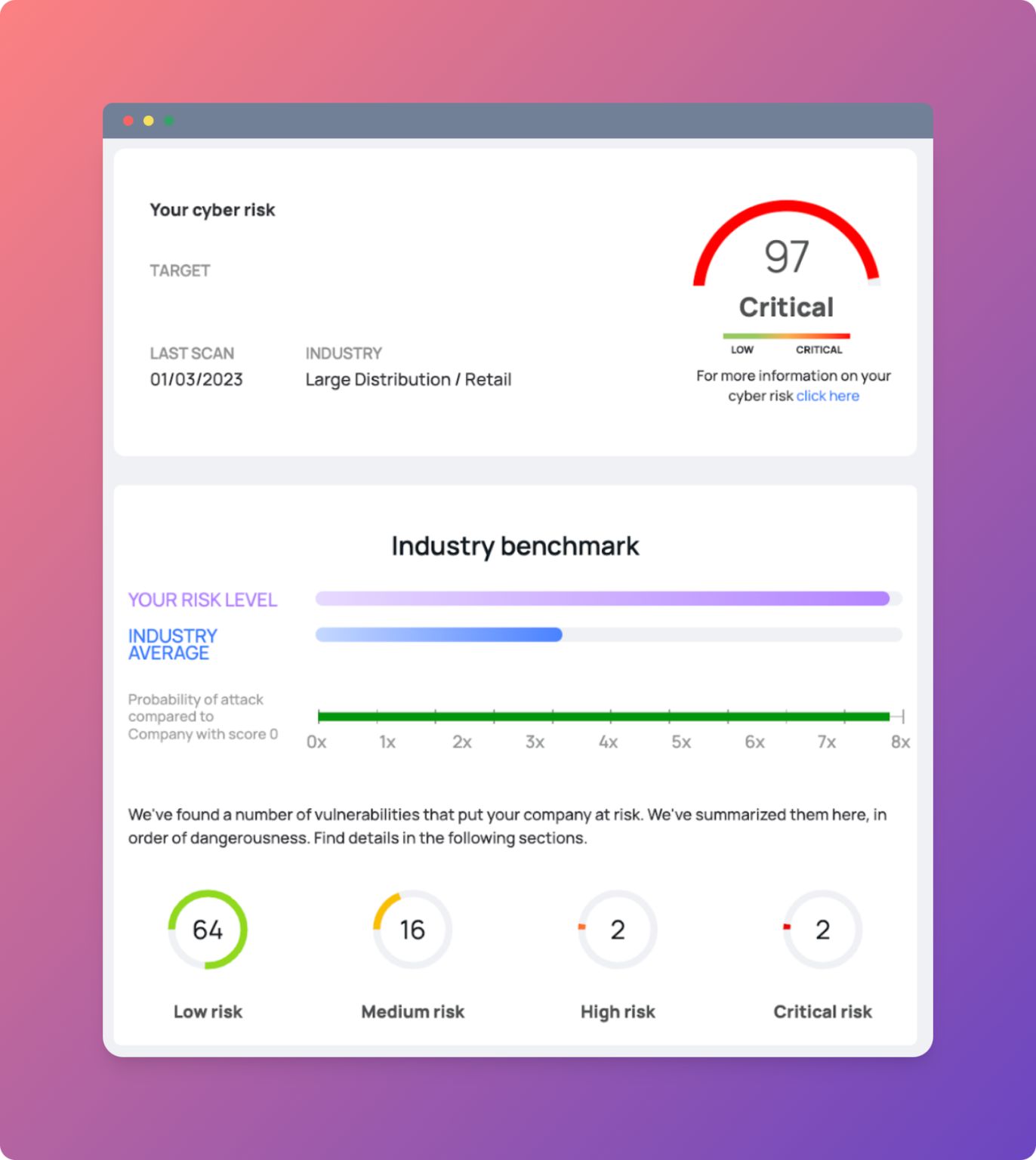
The implementation of the NIS2 directive has come fully into force and will have a major impact on the way companies will have to manage supplier risk in the coming years.
The directive has been in the works since 2016, when it was first proposed by Vice-President of the European Commission Andrus Ansip and the Commissioner for the Single Digital Market Mariya Gabriel during a speech at an event hosted by the European Economic and Social Committee (EESC). In their presentation, Ansip and Gabriel outlined their vision of an updated version of the Network Information Security Directive (NISD)which had been implemented in 2010 but was not particularly effective because it lacked a compliance mechanism.
The Impacts of NIS2 on Small and Medium-sized Enterprises
The NIS2 Directive aims to improve the security of EU information systems and networks.
It requires companies providing essential services to implement a 'comprehensive system' for risk management, including:
- People (employees)
- Physical assets (computers, servers, etc.)
- Systems and data
It also requires all companies to establish a risk management process of its supply chain.
This means that every company operating in the EU must have a clear strategy for working with third-party suppliers.
The Directive applies to all companies (including banks) that use third-party products or services as part of their daily activities.
The most common example is the purchase of computer systems from another company, but there are many more examples. In addition to computers, you may also use software or cloud services provided by other companies: anything purchased directly from them is classified as part of your supply chain for the purposes of NIS2.
The implications will be far-reaching for thousands of organisations: it is estimated that it will affect over 30 million companies across Europe.
NIS2 and supplier management
In addition to this, one of the key components of this directive is the emphasis on the cyber risk management with regard to third-party suppliers.
It is important to understand what NIS2 means by 'third-party supplier' and how it differs from other types of business relations.
The term 'third-party supplier' refers to any company you rely on to obtain goods or services (excluding subcontractors or employees).
So a company you work with is a 'third-party supplier' if you buy a product or service from them.
Suppliers are the cause of attacks
According to a recent report by Ponemon Institute, Deloitte and Shared Assessments Program, the 61% of all IT breaches in the last two years were caused directly by third-party vendors.
In other words, the external providers are more than twice as likely to cause data breaches as internal users. Moreover, these breaches are often caused by security problems that were previously overlooked during an audit.
According to a survey by Forrester Consulting Inc. only the 27% of organisations conduct risk assessments of suppliersi and almost half (48%) has no formal process for third-party risk management.
This means that many companies operate without protection against cyber attacks from their suppliers, or even without being aware that such attacks could occur!
For this reason, the NIS2 directive places special emphasis on identifying and mitigating the risks associated with these suppliers.
As with any other aspect of supply chain management, it is important to ensure that third parties are properly managed. Third parties often provide crucial services such as warehousing, logistics and transport.
As with any other aspect of supply chain management, it is important to ensure that third parties are properly managed. This is because third parties often provide key services such as warehousing, logistics, and transportation.
These services can be used by a company to fulfil its obligations under the NIS2 directive, but they can also be used by cybercriminals who wish to exploit vulnerabilities in your supply chain or steal your data.
This is why the NIS2 directive places great emphasis on identifying and mitigating the risks associated with these suppliers.
How to start managing supplier cyber risk
But how can companies effectively manage the cyber risk of their suppliers?
One solution is theuse of a supplier risk management platform.
In general, a supplier risk management platform enables companies to establish and enforce policy requirements, conduct due diligence on suppliers, monitor their compliance with such policies and standards, and provide a single point of accountability for all relevant information.
For the specific cyber risk, companies can use the platform to assess and manage the cyber risk of their suppliers by securely collecting, analysing and sharing data from multiple sources.
This allows for a holistic view of their supply chain, including the identification of vulnerabilities at each level.
Conclusions
The NIS2 directive is an important step in the fight against cybercrime and data breaches.
Although it may seem overwhelming at first, following a few simple steps can help your organisation stay on top of its obligations and mitigate future risks.
By implementing a supplier risk management platform, companies can not only comply with the NIS2 directive, but also improve the overall security of their organisation. This is a win-win situation: regulatory compliance and increased security.
You can start assessing the cyber risk associated with your suppliers today by requesting free access to our new solution: Cyberangels' Supplier Risk Portal.