We often read news of companies reporting that they have been victims of online scams by people who presented themselves as suppliers or employees, but who turned out to be impostors.
If someone with computer fraud were to succeed in stealing EUR 10,000 from your company (or even EUR 100,000), you might only realise it after a few days and probably have no way of recovering the ill-gotten gains.
But if we told you that there is something we can do right away to significantly reduce the risk of losing all those precious Euros?
Disclaimer - In reality, it is almost impossible to reduce the risk of 100%: the only way to avoid being hacked is to have an unhackable system. Hardly a credible situation.
But there are certainly good practices that can be activated to significantly lower the risk.
If you are reading this article because someone has just asked you to pay your invoice on a new IBAN and you have done so, I am sorry! But don't worry, there are still some things we can do to make sure this doesn't happen again.
There is one thing you can do right away (even if you are not a security expert and do not have anyone to help you see if someone has broken into your systems) and will significantly reduce the risk of losing money.
In fact, it is not so difficult to know 'how much' you are at risk and to take the necessary countermeasures: so, don't wait for a hacker to break into your system to divert your payment flows.
The magic recipe is called continuous monitoring of the attack surface.
What is the attachment surface
A fundamental value for defining your company's IT security is in fact the extent of the "attachment surface".
It sounds complex, but as you will see, it is not.
La attachment surface is the sum of the access points to your company that are visible from the outside (e.g. a device or a network) that an attacker can access and extract data from.
Let's think of it as a bird's-eye view of the company's digital outer perimeter: to make a comparison, it is as if a drone were flying over your house looking for open doors and windows, holes in the fence and more.
It is therefore the set of all known, unknown and potential vulnerabilities that can be exploited to mount a cyber attack or data breach.
Continuous monitoring of the attack surface
It is therefore possible to assess whether the company is exposed to potential cyber security risks or vulnerabilities by analysing the various critical elements that constitute the attack surface and that may be subject to cyber attacks, such as:
- Website
- Personal Data
In this way, you can pre-emptively check what an outside observer may detect when passing outside your home and stop it before it causes damage.
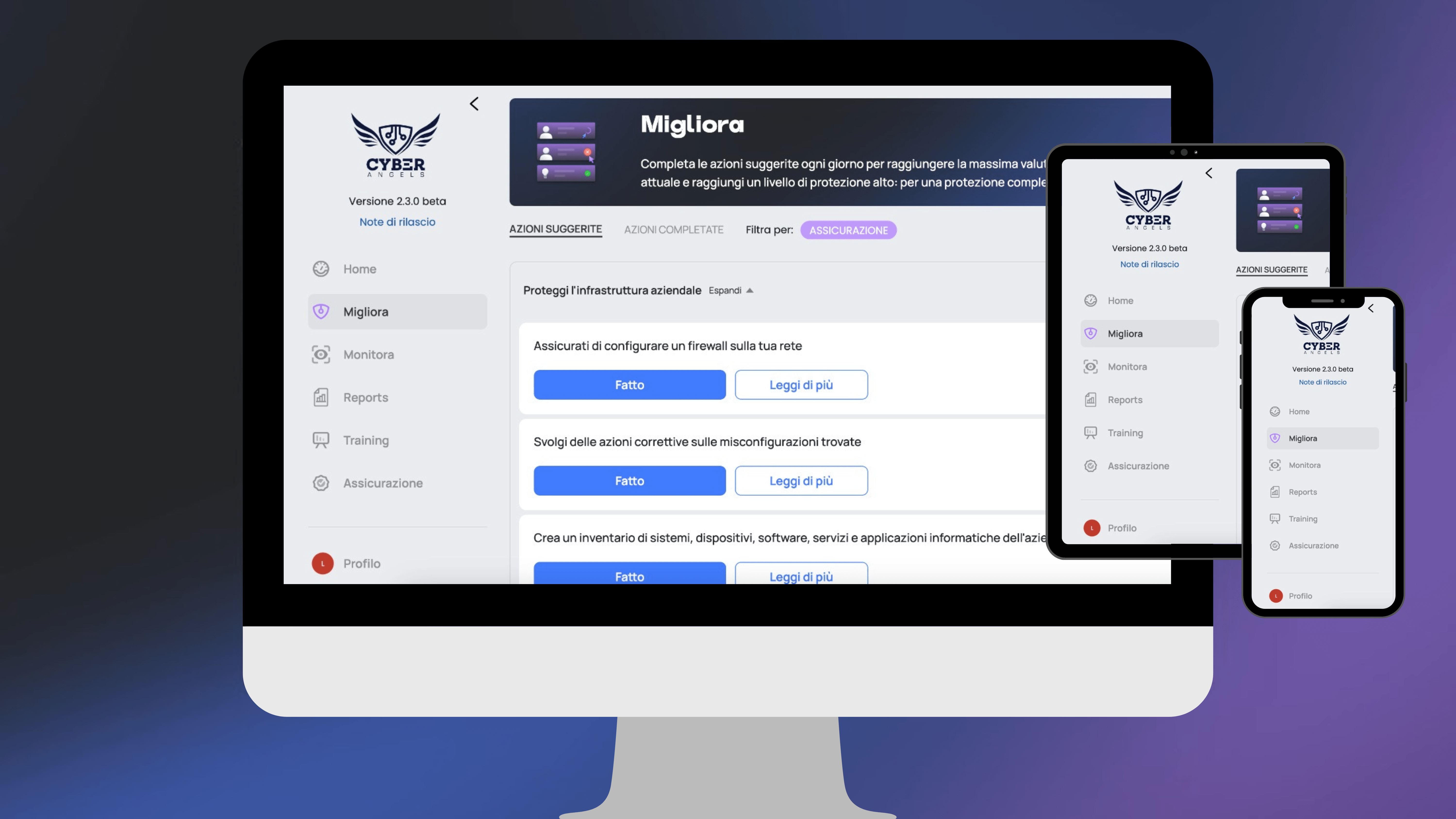
A continuous monitoring tool detects something unusual and sends a message detailing the anomaly, so that users can take the necessary action immediately without having to go through several steps first.
The installation of continuous monitoring and warning systems is extremely cost-effective compared to the risk of having 10,000 euro stolen from your company.
Each Cyberangels subscription includes continuous monitoring of your attack surface. If you are not yet a customer, free trial now for 14 days our service.
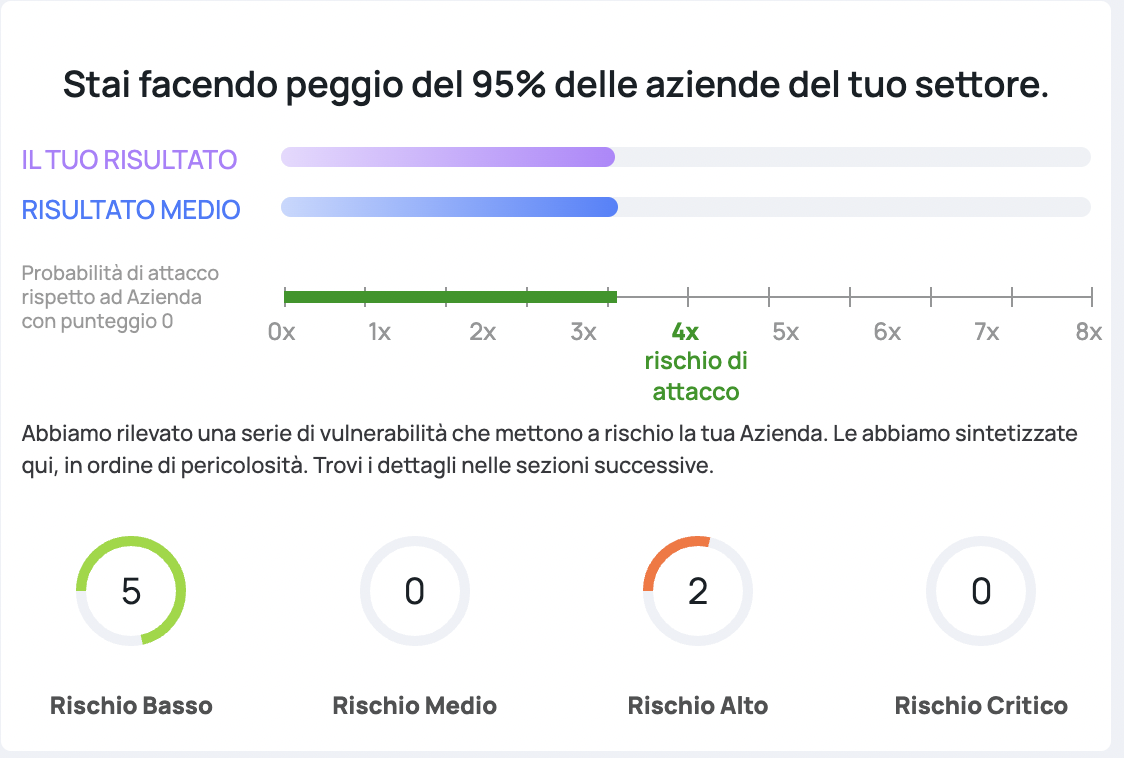
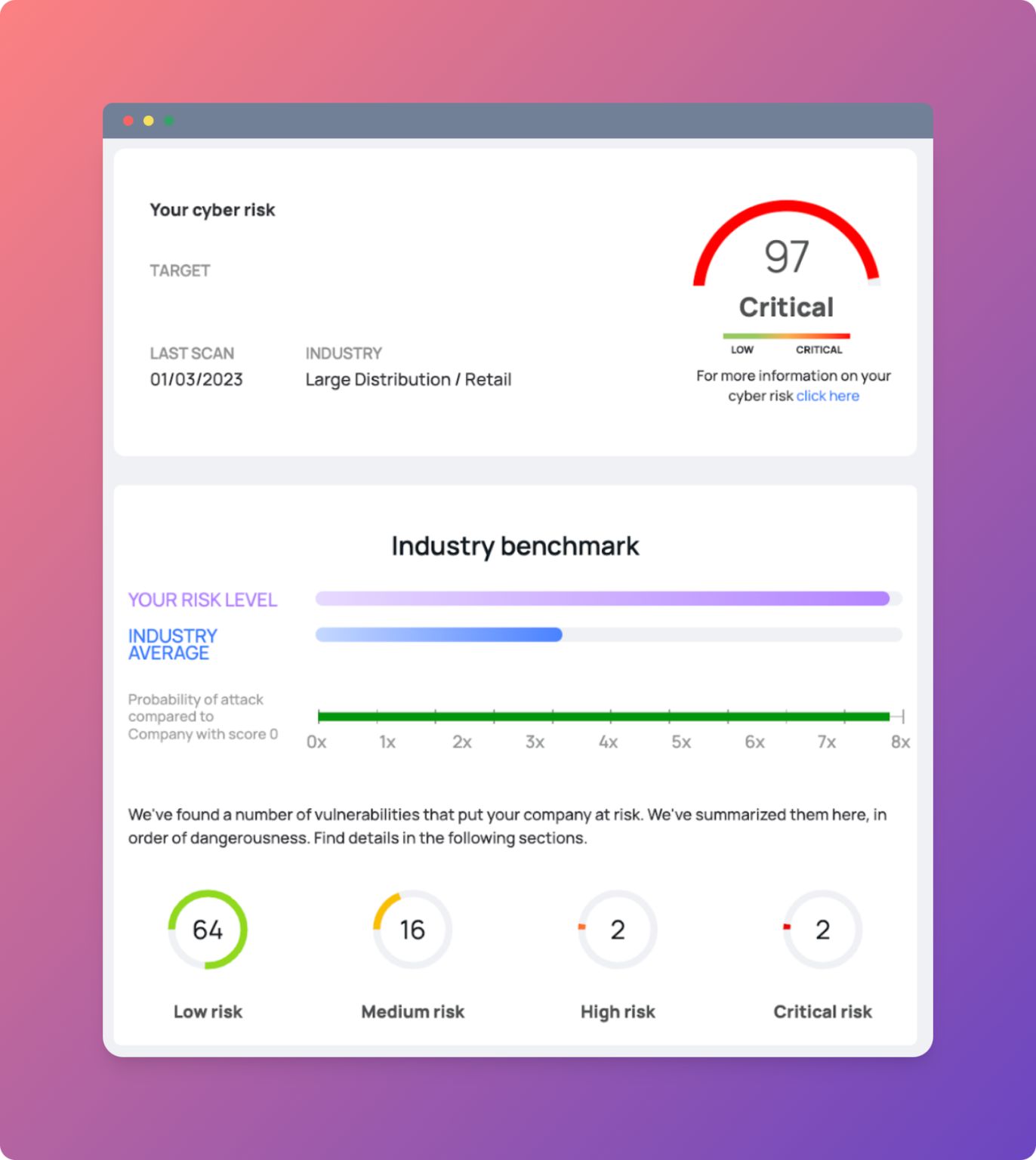
This is an example taken directly from our site:
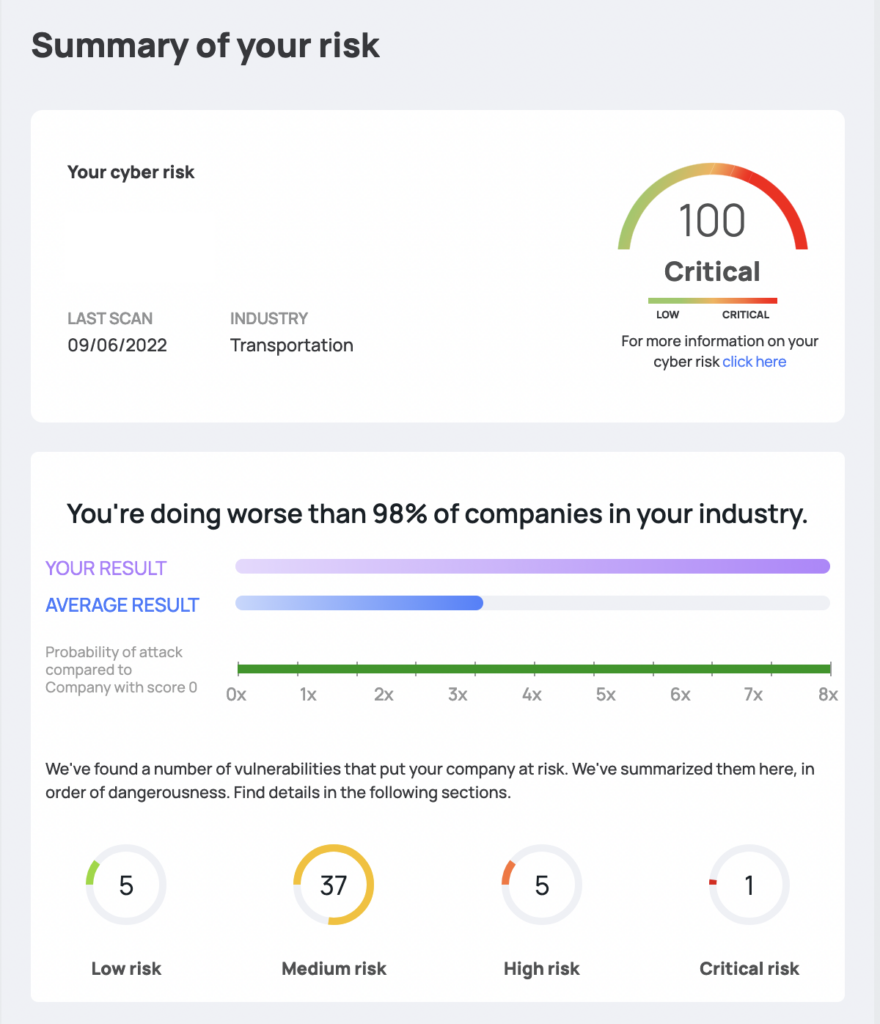
Conclusion
If you are still in doubt as to whether or not you should equip your company with greater protection against cyber attacks, I hope this article has provided you with enough information to understand why it is important and how easy it is to do so.
It is never too late to start protecting your company from hackers. That way we will all be safer!
For any additional information, contact our team and find out with us how you can become as secure as a big company, without necessarily spending capital or hiring specialists.
Let Cyberangels you differentiate yourself from the competition: keep focusing on your business challenges, we'll take care of your security!